This site is all about network monitoring tools, and it would be strange if I didn’t talk about Simple Network Management Protocol. After all, SNMP was the backbone of monitoring for a long, long time. Even today, it is still very much in use for monitoring, but the question is for how long? Let’s find out together how SNMP works using various examples. Learn about differences between SNMP polling and traps? What is the purpose of MIB and OID in SNMP? What is agent and manager? And more!
Table of Contents
SNMP Definition
In this chapter we will define SNMP, discover how you can use it in layman terms, learn a little bit of history and find out which version is the best.
What is SNMP?
SNMP, which stands for Simple Network Management Protocol, is a communication protocol that allows discovery, monitoring, and configuration of SNMP compatible devices that are connected to the network, including routers, switches, servers, printers, and others.
Supported by nearly any manufacturer – from Cisco, Juniper, Huawei, to Microsoft, Linux, Unix and everything in between – SNMP is de facto standard in network and system monitoring (this trend is changing, but more about that later)
The reason for Simple Network Management Protocol popularity is the first word in its name – it is very simple to configure. Only two components are required for SNMP to work: manager and agent.
SNMP agents are installed or embedded on the devices and their primary job is responding to manager inquiries. In other words, agent task is to prepare status and statistics about the system on which it is installed so that it can immediately respond to the manager when prompted.
The SNMP manager, also called NMS (Network Management System), is an application that collects and stores information – from the agents – about end devices. In addition to collecting information, the manager has graphical interface (GUI), where you can check problems, statistics and records of the monitored devices.
Manager (NMS) can use collected information in many ways, I will only name a few:
- device discovery;
- device identification;
- device monitoring;
- performance analysis;
- device management;
- Intelligent notifications, or customizable alerts.
What is SNMP used for?
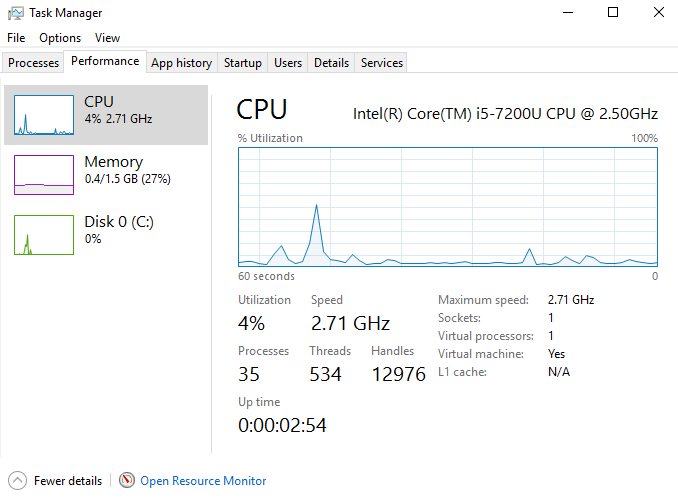
Meet Eric, a junior sysadmin who just got a task from his boss to find out why the company’s application is often slow. Boss said to him: “Check CPU, memory and bandwidth utilization on every server, router and switch on the network!”
Erik rolled up his sleeves and checked every device on the network, and that lasted for hours. He used “Task Manager” for Windows server and “Top command” for Linux to view system performance.
Frustrated by the slow progress and the fact that he is lacking knowledge about computer networks, Eric turned to the almighty Google for help.
All of his search results are saying the same thing: “Use SNMP manager, also referred to as an NMS (Network Management System), to systematically check the health and performance of servers, routers, and switches”!
Eric realized how foolish he was for trying to manually check every device on the network.
He installed the Manager and configured him to check CPU, memory, and bandwidth utilization on every device in the network. After that, Eric enabled an SNMP on every device so they could respond to the Manager.
Manager is way faster than human because it can check every minute the status of hundreds of devices, non-stop, 24/7. In the end, Eric can log in to manager and check graphs like the ones on Task Manager but for every device!
He can also configure the Manager to send him alarm via email if some device has CPU utilization over 90% or when any network interface has 100% usage!
In the picture above, the Manager queries every router and server in the network for the state of CPU utilization. Windows server has a 100% CPU utilization and the manager immediately sends an email to the administrator about this problem. Administrator than connects to the Manager to view history and trends and find out more about the problem.
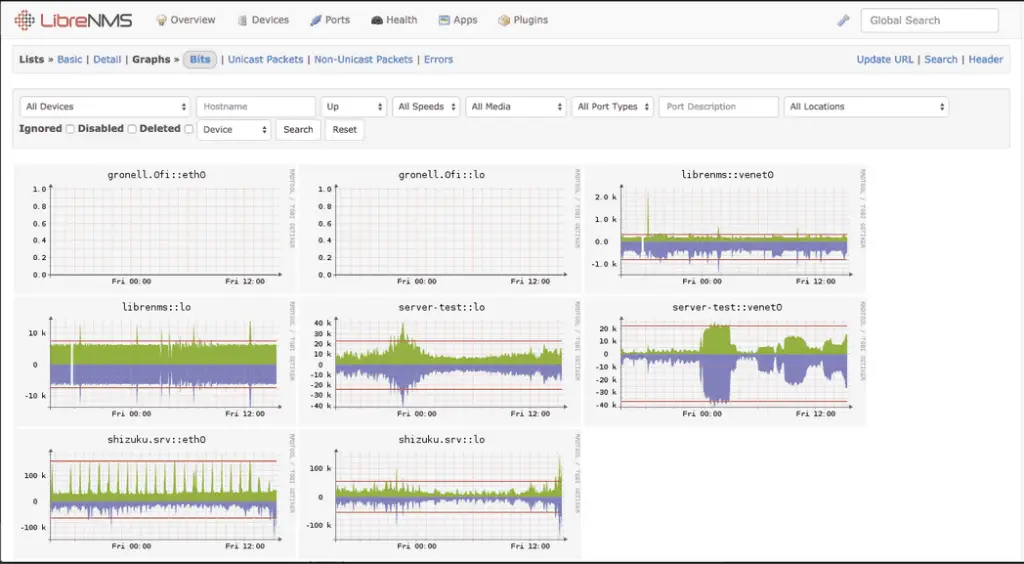
SNMP is not just for monitoring a devices, you can use it for a variety of purposes. For example, Eric received another task from his boss. He must list serial numbers of all the devices on the network.
Now, Eric knows better, he surely will not manually track equipment and write every single serial number on paper. Instead, he will configure monitoring software to do that for him, and later he will only check report.
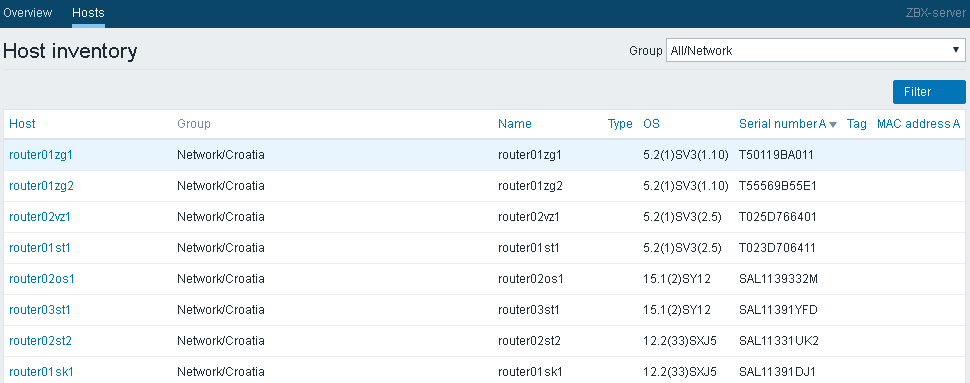
Let’s conclude all this and answer the main question – what is SNMP used for?
SNMP is used to manage network devices such as routers, switches, servers, printers, and others from one central point. It simplifies device management by enabling centralized discovery, monitoring, and configuration of devices on the network.
Here are a few examples to make it easier to understand how SNMP can be used:
- monitor inbound and outbound traffic flowing through the device;
- monitor installed software on Windows servers;
- detection of faults within network devices along with alerts/notifications;
- access and configure devices remotely;
- monitor your servers CPU, memory, disk space usage and alert when thresholds are exceeded;
- send an email or SMS when a device in unreachable via network.
History
As with most innovations, it all starts with a problem – the first major network outage of ARPANET which was the technical foundation of today’s Internet:
On October 27, 1980, there was an unusual occurrence on the ARPANET. For a period of several hours, the network appeared to be unusable, due to what was later diagnosed as a high priority software process running out of control. Network-wide disturbances are extremely unusual in the ARPANET (none has occurred in several years), and as a result, many people have expressed interest in learning more about the etiology of this particular incident.
RFC789
This is a quote from RFC 789 that, back in 1980, warned us about the need for monitoring and managing complex networks.
Soon after that came the first solution: Gateway Monitoring Protocol (SGMP) that is described in RFC 1028 , but in 1988 was quickly replaced with SNMPv1 (RFC 1067) . Then came version 2 followed by version 3 which is recommended version because of the better security.
Few people know that SNMP can configure network devices and that he was trying to replace the command-line interface (CLI) that everyone is using for device configuration.
But the plan failed.
SNMP was great for monitoring but it was rarely used for configuring devices.
Even Internet Architecture Board (IAB), in the early years of 2000, published document (RFC 3535) recommending CLI for configuring things instead of SNMP. After that, IAB launched an investigation to find out why no one wants to use SNMP to configure equipment.
And what they find out? Everyone hates ASN.1 module data structures!
Another issue was security, rather a lack of security in version 1 and 2. No one wanted to enable write-option on devices, while the SNMP passwords (community string) were roaming through the network in plain text. Verision 3 had a security mechanism, but initially, not all devices supported it. Also, people avoid it because of complexity and introduced network overhead.
IAB collected all of those problems and reported them to the IETF (Internet Engineering Task Force).
Soon after that, IETF begin working on the new XML based standard for device and configuration management technology.
At the same time, Juniper Networks developed an XML-based protocol called JUNOScript for managing and configuring theirs devices.
And that’s exactly what the IETF was looking for! A match made in heaven!
IETF took that concept and developed it into standard called NETCONF.
NETCONF is just one of many standards that are trying to replace SNMP.
However, as we all know, migration from one standard to another goes slow (look at IPv4 vs IPv6) so it will probably stay with us for a very long time.
Versions and RFC’s
SNMP has three versions: v1, v2 and v3 and many RFC documents that describe how it works. Bellow, you can find a table that describes all the versions and RFC documents.
| Version | RFC’s | Description |
|---|---|---|
| SNMPv1 | Starting with 1988 various RFCs were released that described SNMPv1. RFCs 1065 and 1066 described various aspects of network management, RFC 1067 titled “A Simple Network Management Protocol” discussed how the ideas in the first two RFCs could be implemented in network management protocol. Those RFCs listed above were updated two years later by RFCs 1155, 1156, and 1157. | SNMPv1 security is based on community strings (plain text password) |
| SNMPv2 | In 1993 RFCs 1441–1452 were proposed. These RFCs revised the previous RFCs and became the basis for version 2. RFCs 1901–1910 were added to RFCs 1441–1452 and created a community-based version of version 2 called SNMPv2c and a user-based version called SNMPv2u. Some people consider the community-based version of SNMPv2 to be the de facto standard. RFCs 1902–1908 describe the community-based version of SNMPv2. | This version has improved performance and communication of the SNMP protocol while introducing new features like GetBulkRequest and Informs. Security did improve in version 2 but because of complexity it was reverted to community based with version 2c (C stands for community. |
| SNMPv3 | In 2002, RFCs 3411,3412,3413,3414,3415,3416,3417,3418 were released that described version 3 and form the basis for the SNMP that we use today | Most secure version , provides secure access to devices using authentication and encryption mechanisms. |
CONGRATULATIONS!
Now you know what is SNMP protocol and how you can use it!
NEXT
Learn how SNMP works (encryption and authentication, difference between SNMP polling and traps, purpose of MIB and OID etc.)
LATER
How can you test SNMP using the command line (CLI)?
What are the best SNMP monitoring tools?
How SNMP works?
SNMP works according to the client-server architecture using these three components:
- Manager – central system that manages and polls remote devices
- Agents – software that responds to Manager inquiries, comes installed or embedded on the managed device
- Simple Network Management Protocol – communication protocol that is used between manager and agent
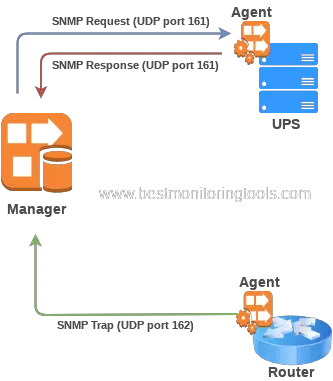
An SNMP manager acting as the client sends requests to one or more agents. Playing the server role, an agent responds according to the manager’s request. An agent can also notify the manager on certain events based on pre-defined criteria using the SNMP trap.
SNMP uses UDP port 161 for sending request and response message types and UDP port 162 for sending traps and informs.
You may have noticed new terminology: poll and trap. Let’s find out what they are!
SNMP Poll vs Trap
What is the differences between polling and traps?
Manager’s main purpose is to collect information about devices on the network by polling agents.
For example, the manager can poll agent, that sits on the router, for the status of a network interface. And it can do that every minute. That process is called polling. When the manager detects that interface utilization is 100% he will trigger an alarm, meaning an email notification will be sent to the administrators.
Agents, besides responding to Manager polls, can independently send a trap when some event occurs.
If only traps are configured on the agent (without polling) then the manager will never query agent for the information, and the agent will keep quiet all until a problem occurs.
When the problem occurs, like a network interface utilization hits 100%, an agent will send a notification to the manager using trap or inform. The manager can then forward that information to the administrator via email.
The relationship between polling and traps is like that of a parent and a school kid.
A kid will report problems with the school to parents only when they occur. Just like the trap is sent only when something goes wrong on the managed device.
But if parents check with the teacher every week on their son progress, they will spot irregularities and prevent problems in time just like SNMP manager does with polling. In that case, parents spend more time and effort, but they know exactly what is going on with their kid.
Like so, an administrator can configure the manager to poll information every minute about devices on the network.That will enable him to configure a weekly report about the utilization of all interfaces on the network. Using that report administrator can plan network upgrades in time and prevent problems with interface utilization. That is only possible with polling!
To conclude, polling gives more information about monitored devices but at the cost of spending more network and system resources. Traps or trapping lacks that information but is more efficient because it is just one-way notification that is triggered when something goes wrong on the monitored device. Trapping requires configuration on each device, which complicates maintenance. Polling is much simpler to maintain because device management is centralized on the manager.
Credentials
A credential is required for the manager to retrieve information from the agent.
Credentials for SNMP version 1 and 2 do not include a username, just a password, called the community string.
The default community string for many SNMP-enabled devices is public when used as read-only, and for read-write is private. Community-based authentication is not secure because there is no encryption; a password is sent over the network in a plain-text format.
Version 3 is recommended because of authentication and encryption support.
The SNMPv3 supports the following set of security levels (RFC 2574):
- noAuthnoPriv – Communication without authentication and privacy.
- authNoPriv – Communication with authentication and without privacy. The protocols used for authentication are MD5 and SHA (Secure Hash Algorithm).
- authPriv – Communication with authentication and privacy. The protocols used for authentication are MD5 and SHA; and for Privacy, DES (Data Encryption Standard) and AES (Advanced Encryption Standard).
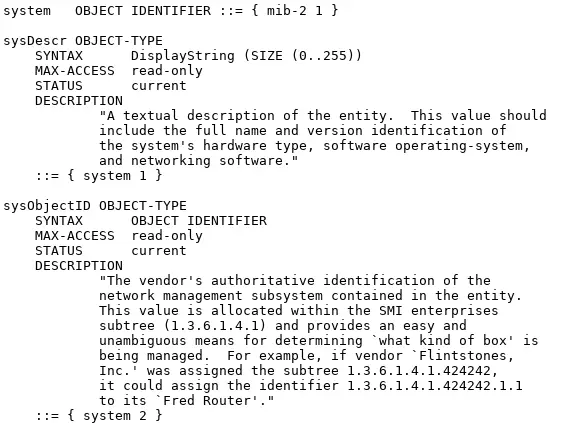
Purpose of MIB and OID in SNMP?
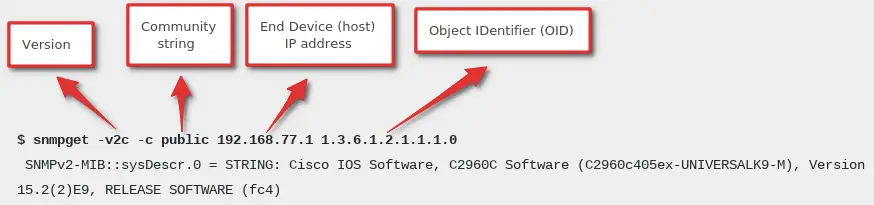
To get information from an SNMP-enabled device, you need that devices IP address, Community string and OID (Object IDentifier).
Object identifiers (OIDs) are used in numeric format separated by periods like this “1.3.6.1.2.1.1.3.0”.
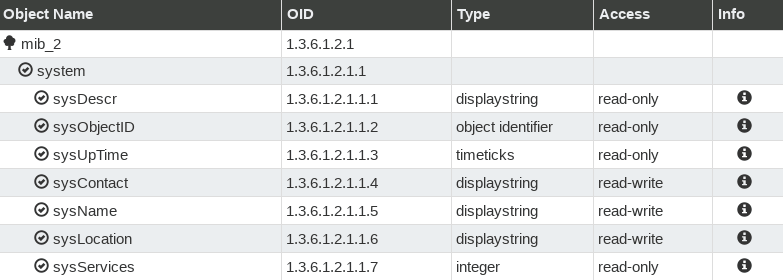
There can be thousands of OID’s on the device and each of them is a unique identifier of a specific piece of information. For example, if you use OID 1.3.6.1.2.1.1.3.0 to query the device for the information you will get system uptime as an answer. And with “1.3.6.1.2.1.1.1” (sysDescr) you will get a description of the system.
Let’s try that! Here is an example on how can you get system description from any SNMP-enabled device using Net-SNMP tools:
As you can see in the example above, you can query SNMP-enabled devices using some OID’s and it will give you some information — a number (like 431721265), a string (like “Cisco IOS Software, C2960C Software”), or any of the other information types (more about Net-SNMP tools in section SNMP testing tools).
In conclusion, an OID is a numerical address used to check the status of the components on network devices (like CPU, memory, power supply, network traffic, etc.).
Different types of devices (routers, servers, printers, etc.) provide different information through SNMP. Some devices only provide a few pieces of information (like name, uptime, and serial number); others can give you any information about the device (like routing table, temperature, interface utilization, etc).
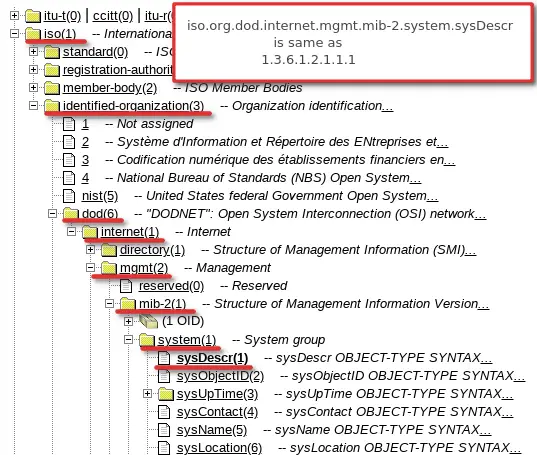
There are millions of OIDs today, we have universal OIDs that are supported on every type of equipment. And additionally every type of device brings its own OIDs. That’s a lot of OIDs! Fortunately, there is an order in that sea of OIDs! That order is called Management Information Base (MIB).
Simply put, the MIB is a collection of OIDs that contains information about the type of information each OID provides and their human-readable names.
Let me give an example – MIB called RFC1213 (MIB-2) has OID “1.3.6.1.2.1.1.1” that is defined as “sysDescr” with data type “string”. That OID can be written as 1.3.6.1.2.1.1.1 or as 1.3.6.1.2.1.1.sysDescr. You can define the rest of the numbers in that OID, so you could write “iso.org.dod.internet.mgmt.mib-2.system.sysDescr” instead of “1.3.6.1.2.1.1.1” – they are the same thing.
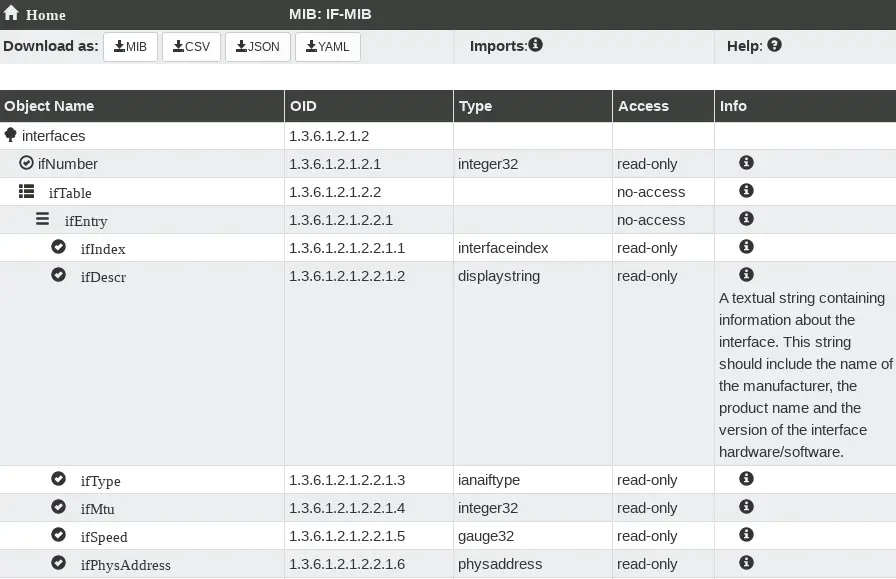
A MIB is written hierarchically. In the image below you find an example of MIB IF-MIB that defines all the OIDs under OID 1.3.6.1.2.1.2 (1.3.6.1.2.1.2.2.1.2 and its children, 1.3.6.1.2.1.2.2.1.3 and its children, etc.).
You can check this video if you are still confused about MIB, OIDs, traps, polling…
CONGRATULATIONS!
Now you know how SNMP works!
NEXT
How can you test SNMP using the command line (CLI)?
What are the best SNMP monitoring tools?
SNMP testing tools
One of the best tools on Linux for testing SNMP is Net-SNMP. Using that tool I will show you how to use SNMP on Linux. There is also a Windows version of the Net-SNMP tool but I recommend the SnmpB MIB browser instead to test SNMP and manage MIBs on Windows.
On Ubuntu/Debian you can install it with one simple command: “apt-get install snmp” or if you have CentOS/RHEL you can use “yum install net-snmp net-snmp-utils“.
Using Net-SNMP commands we are gonna find out routers model, serial number, and network interfaces statuses and descriptions. After that we will shutdown one network interface on the router using snmpset command.
To find out system description on the router we will use OID 1.3.6.1.2.1.1.1 called sysDescr from RFC1213 (MIB-2).
On your linux terminal use snmpget command to poll information from end device. Define community string (my is public) and IP addres of router (my is 192.168.1.1):
$ snmpget -v2c -c public 192.168.1.1 1.3.6.1.2.1.1.1.0
SNMPv2-MIB::sysDescr.0 = STRING: Cisco IOS Software, C2960C Software (C2960c405ex-UNIVERSALK9-M), Version 15.2(2)E9, RELEASE SOFTWARE (fc4)
Technical Support: http://www.cisco.com/techsupport
Copyright (c) 1986-2018 by Cisco Systems, Inc.
Compiled Sat 08-Sep-18 16:49 by prod_rel_team
To find out serial number use OID 1.3.6.1.2.1.47.1.1.1.1.11.1001 from MIB ENTITY-MIB:
$ snmpget -v2c -c public 192.168.1.1 1.3.6.1.2.1.47.1.1.1.1.11.1001
.1.3.6.1.2.1.47.1.1.1.1.11.1001 = STRING: "FCW1139B4SX"
We will use the snmpwalk option to “walk” through all OID’s for interface status: ifOperStatus (1.3.6.1.2.1.2.2.1.8) from MIB IF-MIB:
$ snmpwalk -v2c -c public 192.168.1.1 1.3.6.1.2.1.2.2.1.8
.1.3.6.1.2.1.2.2.1.8.1 = INTEGER: up(1)
.1.3.6.1.2.1.2.2.1.8.10101 = INTEGER: down(2)
.1.3.6.1.2.1.2.2.1.8.10102 = INTEGER: down(2)
.1.3.6.1.2.1.2.2.1.8.10103 = INTEGER: down(2)
.1.3.6.1.2.1.2.2.1.8.10104 = INTEGER: down(2)
.1.3.6.1.2.1.2.2.1.8.10105 = INTEGER: up(1)
.1.3.6.1.2.1.2.2.1.8.10106 = INTEGER: down(2)
.1.3.6.1.2.1.2.2.1.8.10107 = INTEGER: down(2)
.1.3.6.1.2.1.2.2.1.8.10108 = INTEGER: up(1)
What’s wrong with that result? We have some interfaces in UP state and some that are DOWN but we only know index number like “.10102” is down, and 10105 is up. We need to find out interface descriptions like Ethernet0/4, Vlan100.
To get interface descriptions, we will use OID ifDescr (1.3.6.1.2.1.2.2.1.2):
$ snmpwalk -v2c -c public 192.168.1.1 1.3.6.1.2.1.2.2.1.2
.1.3.6.1.2.1.2.2.1.2.1 = STRING: Vlan1
.1.3.6.1.2.1.2.2.1.2.10101 = STRING: GigabitEthernet0/1
.1.3.6.1.2.1.2.2.1.2.10102 = STRING: GigabitEthernet0/2
.1.3.6.1.2.1.2.2.1.2.10103 = STRING: GigabitEthernet0/3
.1.3.6.1.2.1.2.2.1.2.10104 = STRING: GigabitEthernet0/4
.1.3.6.1.2.1.2.2.1.2.10105 = STRING: GigabitEthernet0/5
.1.3.6.1.2.1.2.2.1.2.10106 = STRING: GigabitEthernet0/6
.1.3.6.1.2.1.2.2.1.2.10107 = STRING: GigabitEthernet0/7
.1.3.6.1.2.1.2.2.1.2.10108 = STRING: GigabitEthernet0/8
Let’s say that Interface GigabitEthernet0/5, with the index number “.10105”, is used for guests in the meeting room. And now that meeting is over, for security reasons, it should be administratively down
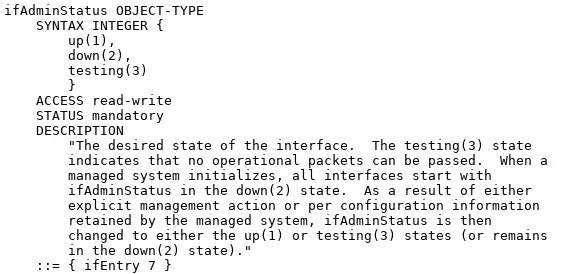
To administratively shutdown interface, we will use OID ifAdminStatus (1.3.6.1.2.1.2.2.1.7) with snmpset option:
snmpset -v2c -c private 192.168.1.1 1.3.6.1.2.1.2.2.1.7.10105 i 2
IF-MIB::ifAdminStatus.10105 = INTEGER: down(2)
And that’s Net-SNMP tools in a nutshell!
Need more examples? Check out my post about snmpwalk, snmpget, snmpset and snmptrap examples using SNMP v2 and v3.
SNMP monitoring software
The SNMP manager (NMS) is monitoring software that collects and stores information – from the agents – about end devices. In addition to collecting information, the manager has a graphical interface (GUI), where you can check problems, statistics, and records of the monitored devices.
There are great monitoring tools out there that fully supports SNMP, but which one to choose? Well, it depends on your needs.
If you need a free and full-fledged monitoring system to monitor your entire IT infrastructure and services then I recommend using Zabbix because of his 100% open-source politics and excellence. You can check out my quick Zabbix installation guide for Ubuntu, Debian, CentOS/RHEL and Raspberry Pi.
Other honorable mentions are Prometheus in combination with Grafana, or Icinga, LibreNMS, OpenNMS, Nagios Core.
All of the tools I mentioned above are free and open-source. I’m a big fan of the open-source movement, I even wrote a time-travel article about open-source. However, I have to admit that, among commercial tools, PRTG amazed me with its simplicity. It’s practical and user-friendly tool that can be installed on Windows and configured in minutes – check the pricing and give it a try if open-source is not your thing.
Conclusion
Simple Network Managment Protocol (SNMP) simplifies device management by enabling centralized discovery, monitoring, and configuration of devices (routers, switches, printers and others) on the network.
SNMP is an almost universally supported, simple, well-known, and free protocol that is helping us to manage network devices for more than 30 years.
Despite everything, the trend shows that his days are numbered! Want to know more? Continue reading:
Thank you for reading.




A crisp yet sufficient to have the first time idea about SNMP and NMS … GREAT
This is the best information and tutorial that I found.
Great article! Systematically explain the SNMP things. Thanks a lot!
It was a great lesson, it helped me a lot.
Thank you very much.
The best piece on SNMP so far! Thanks!
Excelent article
Good Article, appreciate!